Windows Server Hacks: Remotely Enable Remote Desktop
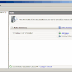
Remote Desktop is a cool feature of Windows Server 2003 that lets you remotely log on to and work at a machine as if you were seated at the local console (in Windows 2000 Advanced Server, this feature was called Terminal Services in Remote Administration Mode). Remote Desktop can be a lifesaver for fixing problems on servers at remote sites, but what if you forgot to enable the feature before you shipped the server out to Kalamazoo? Enabling Remote Desktop is easy if the server is in front of you: just log on as an administrator, open System in Control Panel, select the Remote tab, and under Remote Desktop select the checkbox labeled "Allow users to connect remotely to this computer." Unfortunately, you can't use the System utility to enable Remote Desktop on a remote machine, though you can access some properties pages of System using Computer Management by first connecting the console to a remote computer, then right-clicking on the root node and selecting Properties. Unfortunately, as you can see in Figure 1 below, the Remote tab is not available when you access System properties this way on a remote machine (here named SRV220).
Figure 1. System properties for a remote machine does not have Remote tab
Fortunately, there's a workaround. Sit down at your desk and log on to your Windows XP workstation using your administrator credentials and start Registry Editor by Start --> Run --> regedit --> OK. Then select the Connect Network Registry option under the File menu (Figure 2).
Figure 2. Connecting to the Registry on a remote machine.
This opens the Select Computer search box. Either browse Active Directory to locate the remote server, or type its name in the textbox (Figure 3).
Figure 3. Connecting to the Registry on a remote server named SRV220.
Click OK and a node will be displayed in Registry Editor for the remote machine (Figure
Figure 4. HKLM and HKU hives on SRV220.
Now browse HKLM on SRV to find the following Registry key (Figure 5).
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server
Figure 5. Registry key for Terminal Server on remote machine.
Under the Terminal Server key, you'll find a REG_DWORD value named fDenyTSConnection. Double-click on that value to open theEdit DWORD Value box and change the value data from 1 (Remote Desktop disabled) to 0 (Remote Desktop enabled), as in Figure 6 below.
Figure 6. Set fDenyTSConnections to 0 to enable Remote Desktop on SRV220.
The remote machine needs to be rebooted for the change to take effect, so open a command prompt and type the following command:
shutdown -m \\srv220 -r
After the remote machine reboots, Remote Desktop should be enabled on it. To test this from your workstation, open Start --> All Programs --> Accessories --> Communications --> Remote Desktop Connection, enter the name of the remote server in the Remote Desktop Connection logon box, supply your administrator password when prompted, and you're in.